|
How to Hack an Email
Learn how to hack an email quickly and for free with the following techniques that we will recommend in this post. Read on! 😈
Explanation Images
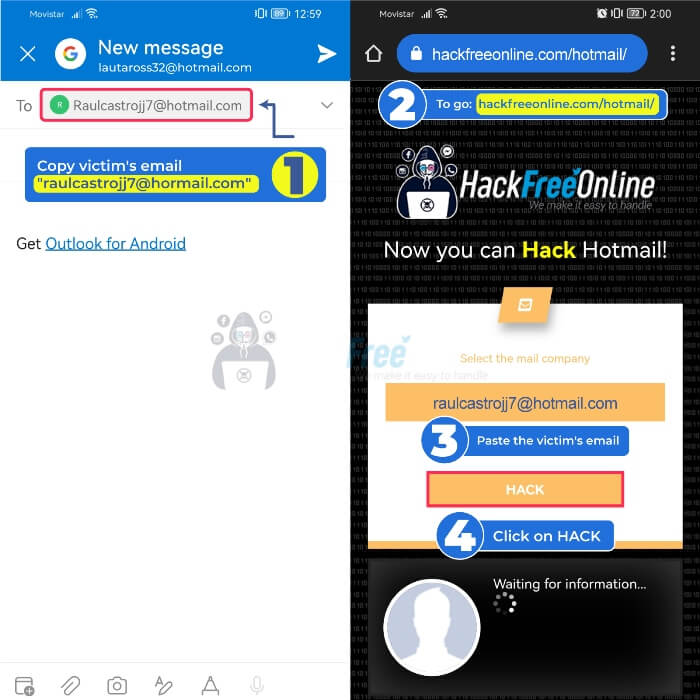
📱 Steps to Hack an Email from a mobile phone
- 1️⃣Enter the inbox and copy the email address of the person you want to hack by clicking on the three dots
- 2️⃣Go to www.hackfreeonline.com/email
- 3️⃣Paste your victim's address in the main field
- 4️⃣Finally, click on "Hack"
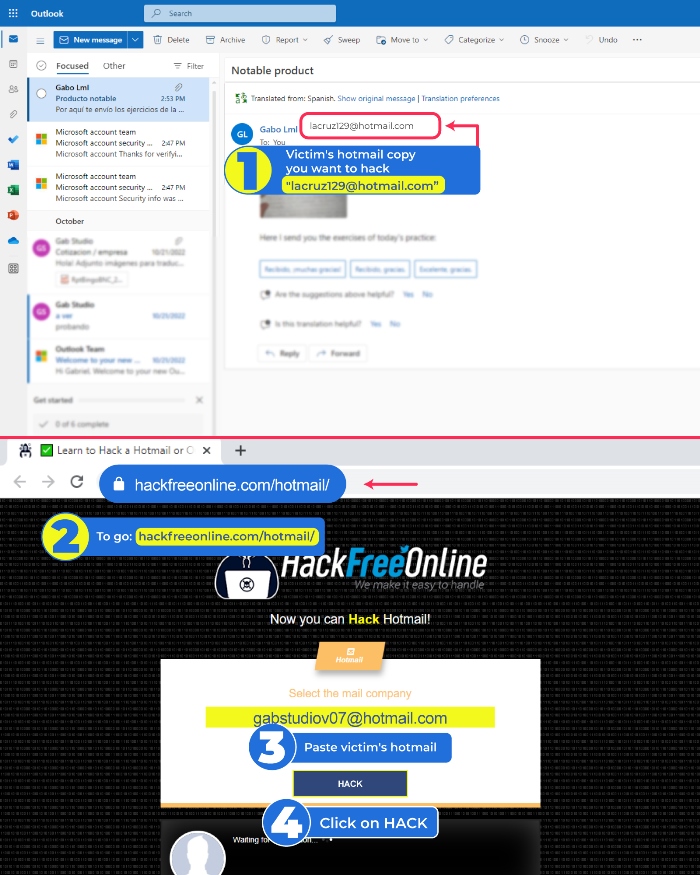
💻 Steps to Hack an Email from a computer
- 1️⃣Access the inbox and copy the email address of the person you want to hack
- 2️⃣ Go to www.hackfreeonline.com/email
- 3️⃣Paste your victim's link in the main field
- 4️⃣Finally, click on "Hack"
⭐ Hack Email with hackfreeonline
Email hacking websites are becoming more and more popular, thanks to their effectiveness. One of the best options is hackfreeonline.com which allows you to hack an email account in a matter of minutes, following simple steps and you will not be exposed during the process.
With this system you can hack any Email account in a few minutes, without having to download any program or pay anything. Likewise, you do not need to have computer experience or knowledge to use this website.
In a matter of minutes you will be able to download the credentials to access the account. The advantage of using this system is that you can hack an Email from any device, you only need Internet access.
Hack Email with Phishing
A second strategy to hack an Email account is Phishing, this technique consists of tricking users into entering their access credentials on a fake web page that imitates the appearance of almost any legitimate portal.
Under this method, it is much easier and more convincing to obtain the data or credentials of the Email accounts you want. Phishing consists of hacking email accounts and is usually carried out through emails that simulate being sent by the platform itself.
One way to use Phishing is through SCAM, this is a form of email scam. It seeks to trick recipients into sending them money or personal information.
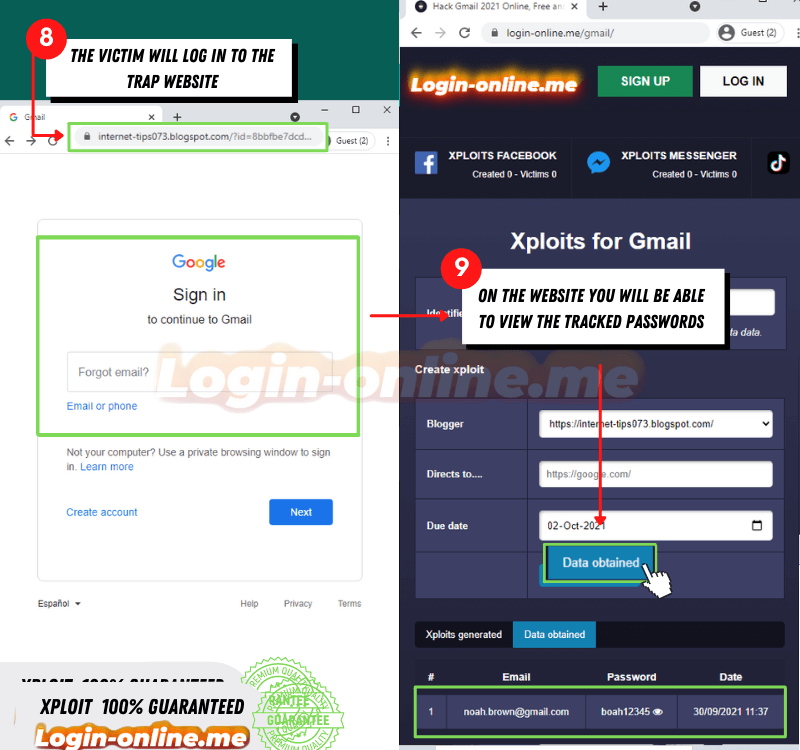
The goal of a SCAM is to gain access to victims' online accounts, steal their identity, extort money from them, or simply keep their money. If you want to create a SCAM you can use Login-online.me
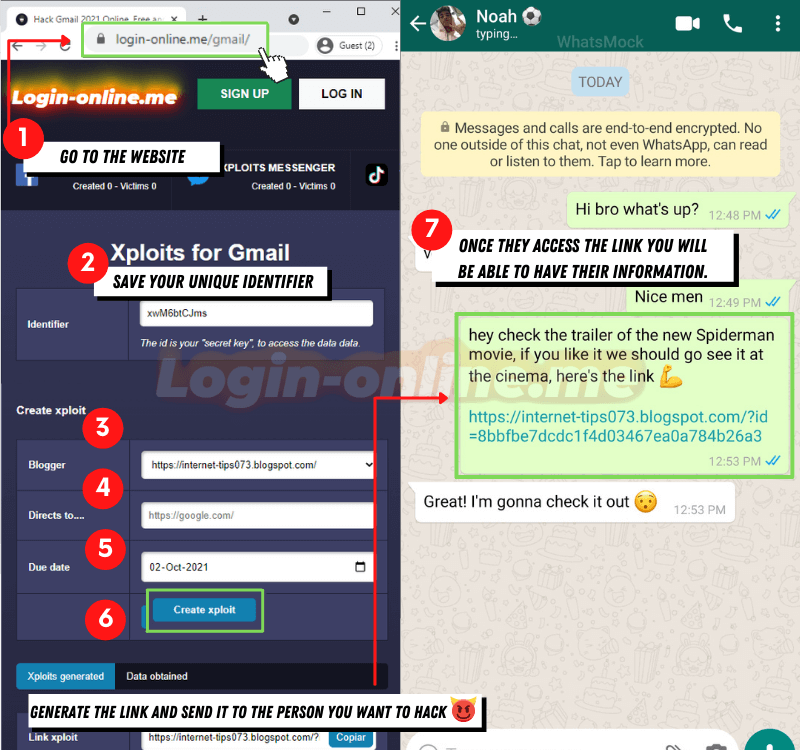
- Go to https://login-online.me/gmail/
- Save the identifier
- Select an attractive blogger to wich the person you want to hack will be attracted
- Select a link where the victim will be redirected
- Set an expiration date
- Click on "create SCAM"
- Send the link to the victim with a message that generates trust and is convincing so that the person can access it with confidence.
- Now wait for the person to enter their data, and then you can view it on the platform and hack Outlook. It's really easy! ✅
Hack Email with Keylogger
Keyloggers are software that records the victim's keystrokes and activity remotely. Usually the victim is unaware of the existence of this program on their devices, which is why it is so attractive and efficient.
A keylogger can be a good tool to steal personal data, passwords or email account information. A reliable page is https://keylogger.shop/
To use the keylogger all you have to do is install the software on the device of the person you want to spy on. Whether through a malicious web page, a contaminated application or direct access to the computer.
Then, you must wait for the person to log into their Email account and obtain the credentials they type.
Hack Email with FORM-GRABBING
Hacking Email with FORM-GRABBING is another 100% effective technique to obtain data and full access to an Email account. It is essential to know certain basic fundamentals of programming or computing to make correct use of this tool.
FORM-GRABBING consists of a form that collects information, data, users, passwords and more from any account or person. This data is intercepted by a virus or malware that the third party innocently opens on their device.
This method can be undetectable to the victim and their devices. It is designed to affect any web platform, not just Email accounts. In addition, it can give you access to the most sensitive information of Email accounts, such as photos, inbox, outbox, important settings, GPS location and more.
Hack Email with malware and viruses
Viruses and malware have been very common methods to infiltrate devices and hack an Email account. The negative of these methods is that it is not only used to hack, but also to disable a computer or make it unusable for life.
In this section we discuss the most common types of attacks:
- Malware: is malicious software designed to damage or infiltrate a computer system without the user's consent.
- Virus: It is a type of malware that spreads and infects files or programs in a computer system, replicating and causing damage or alterations in its operation.
- Spyware: is a type of malicious software that is installed on a system without the user's knowledge and collects personal information, such as passwords, banking details or browsing habits, to send to third parties without consent.
- Adware: is software that displays unwanted advertisements on a computer system, usually in the form of pop-ups or banners, with the aim of generating revenue for the creator of the program.
- Trojans: are a type of malware that disguise themselves as legitimate programs, but actually contain malicious code. These programs trick users into installing them and allow them to access and control the system remotely, without the user's knowledge.
- Spoofing: is a technique in which an attacker forges the identity or source address in a message, data packet, or communication, in order to trick recipients into believing that it comes from a legitimate source
- Hijacking: refers to the action of taking control of a system or resource in an unauthorized manner
Tips to Keep my Email Secure
Security of your email is essential to protect your personal information and avoid threats such as identity theft or phishing. Here are a few tips to keep your email secure:
- Avoid weak passwords: Use a unique, strong password for your email. Avoid easy-to-guess passwords and change them periodically.
- Don't share your password: Never share your password or respond to emails that request your personal information, as these could be phishing attempts.
- Two-step verification: Turn on two-factor authentication, which adds an extra level of security by sending a code to your mobile phone or alternate email every time you sign in from a new device.
- Monitor activity: Review your recent account activity and control which devices, locations, and apps have access. Log out of unrecognized devices and revoke access to suspicious apps. Also configure recovery options.
- Email encryption: When you need to send sensitive information, such as passwords or banking details, use encryption tools such as PGP or S/MIME to protect the content.
- Be careful with emails: Be cautious when opening emails, especially if they contain attachments or links. Avoid opening messages from unknown or suspicious senders. Use an antivirus or malware scanner before opening files.
- Blind Copy (BCC): uses the blind copy option (BCC) to protect the privacy of recipients.
- Mail Forwarding: Be careful when forwarding emails to avoid sharing additional unwanted information, such as conversation histories or addresses of other recipients. Review and modify content before forwarding it.
By following these tips, you can strengthen your email security and protect your personal data from cyber threats.