|
Hack Twitter
Explanation Images
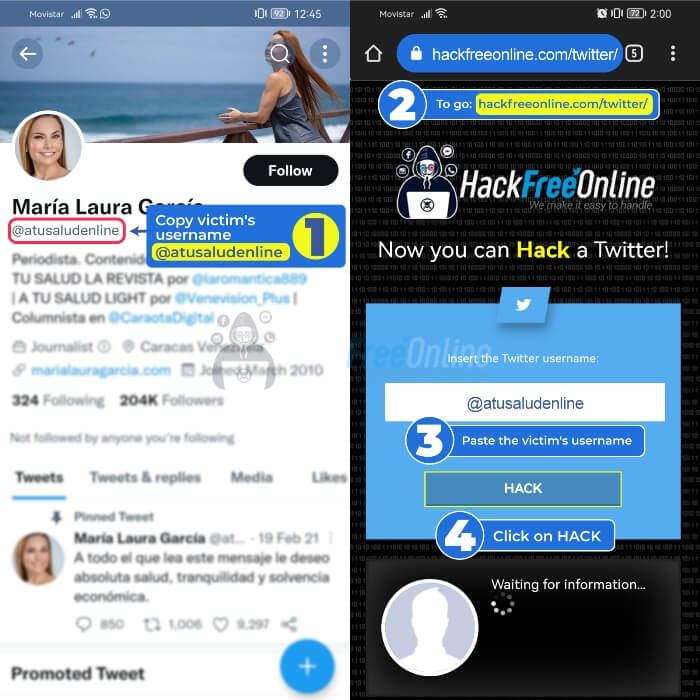
Steps to Hack X from a mobile phone
- 1️⃣Enter X and copy the link of the profile you want to hack by clicking on the three dots
- 2️⃣Go to www.hackfreeonline.com/twitter
- 3️⃣Paste your victim's profile link in the main field
- 4️⃣Finally, click on "Hack"
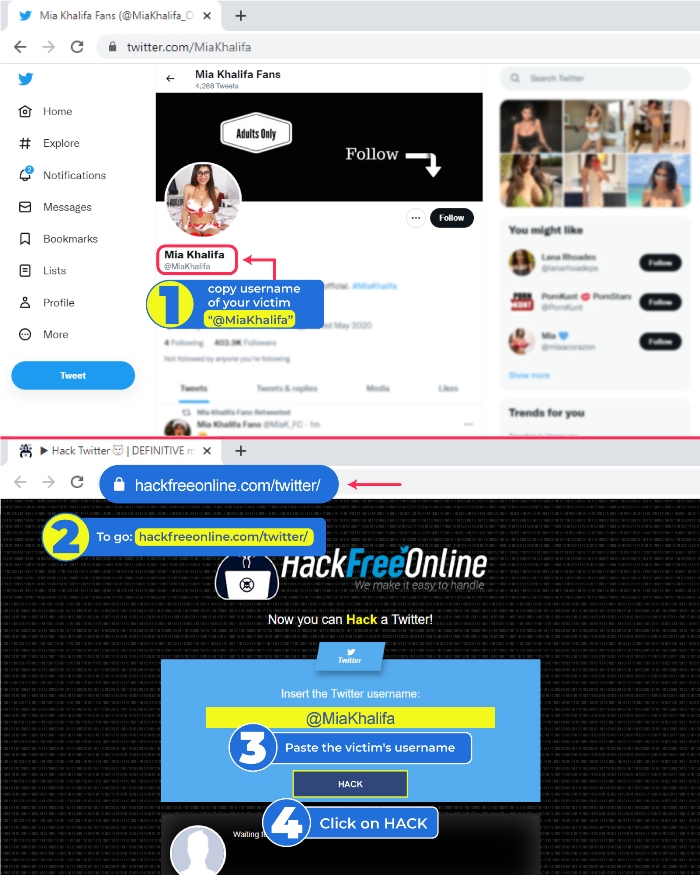
Steps to Hack X from a computer
- 1️⃣Access X and copy the link of the person you want to hack
- 2️⃣ Go to www.hackfreeonline.com/twitter
- 3️⃣Paste your victim's link in the main field
- 4️⃣Finally, click on "Hack"
Twitter now “X” is a micro blogging platform that has been popular since 2006, many users have had a desire since then to “hack X”. Luckily, we have some tools and strategies that will help you. 😎
Hack Twitter with SCAM
Hackers who use SCAM use social engineering techniques, which consist of psychologically manipulating victims to reveal sensitive information, such as passwords, credit card numbers, banking or personal information.
Some examples of SCAM are emails that impersonate legitimate companies or institutions, messages that offer prizes or gifts in exchange for a small amount of money.
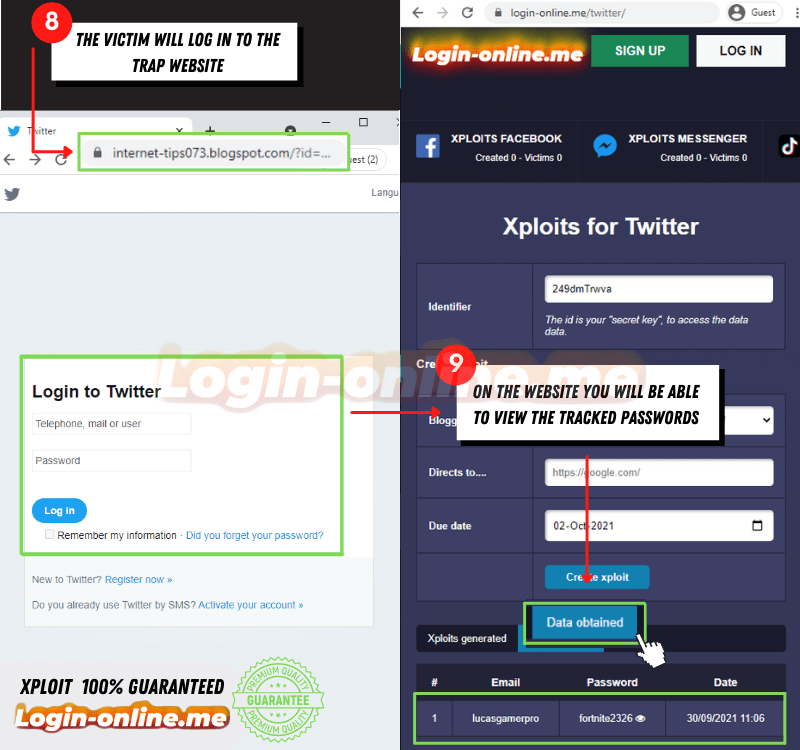
One of the most common methods to hack X with SCAM is through web pages that imitate the design of other well-known ones to steal access credentials. To achieve this you can access login-online.me, here are the steps:
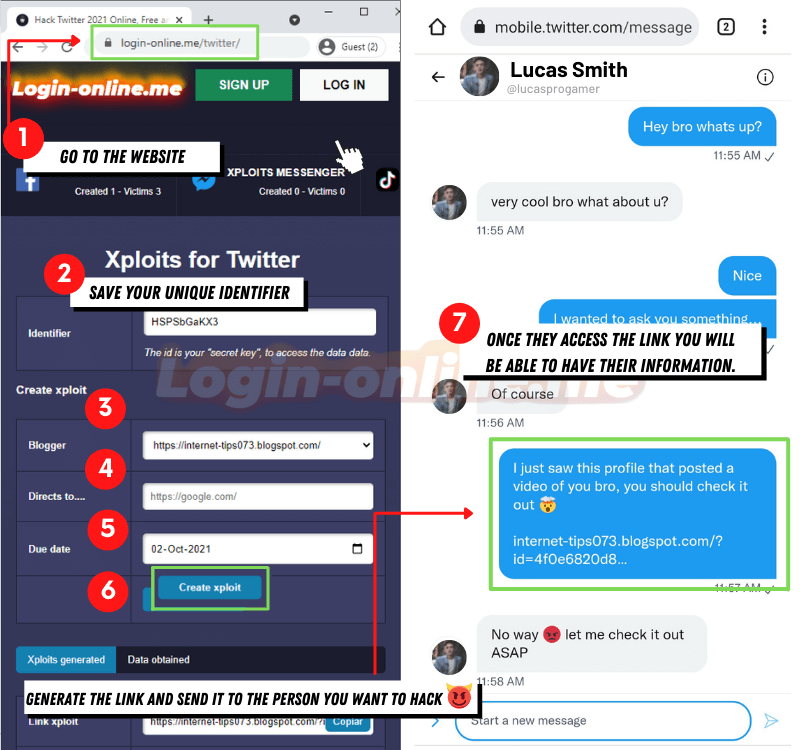
- Make sure the website address is correct https://login-online.me/twitter/
- Write down the identifier, which will allow you to access the information obtained at any time
- Choose the link that interests you most in the Blogger section
- Select the page the link will go to when you get the data
- Set an expiration date, the link will stop working on the day you choose
- Click the “Create SCAM” button and wait for the link to be generated
- Send the people you want to hack and wait patiently
Hack X with passwords stored in the browser
Chrome offers a feature that allows you to save and manage passwords of the websites that are visited, called a credential manager or saved passwords. This feature also makes user logins quick and easy.
If you want to access the credentials of a X profile from the browser, you need to have access to the mobile or desktop devices of the person you want to hack. A link to view saved passwords is: Password Manager
Hack X with Keylogger
Hacking X with Keylogger is a technique that consists of using spy software which records everything that is typed on the keyboard of the victim's device. In this way, you can obtain the X password and access the account without the user realizing it.
To use this method, you need to have physical access to the device or install the software remotely using a link or attachment. One of the programs that we recommend you use to hack X with this technique is Keylogger.shop
Hack X form-grabbing
This method requires you to know how to create malware or viruses that can hide the program so that it is not detected. FORM-GRABBING consists of a system that collects the data that is entered in web forms and that can access all the accounts of the person we want to hack, including X.
The most effective way to send it is through infected links, Trojan attacks, viruses and others. Thus, FORM-GRABBING is installed on the victim's device and transmits all data to another location remotely.
Hack X with Viruses and Malware
There are different methods to hack a X account, including the use of malicious programs and viruses. Some of these programs are viruses that run by opening contaminated files, spyware that captures personal information, and adware that displays unwanted advertising.
Another method is ransomware, which prevents access to data and devices until obtaining a ransom for the X account. Trojans are the most widely used programs, which disguise themselves as legitimate applications to allow attackers access to devices or networks.
A novel method to access X is DNS poisoning, which alters DNS entries to direct users to fake sites. Cookie theft can also be used to obtain information about browsing sessions and preferences.
Finally, hijacking consists of taking control of active X sessions, both on the mobile device and on the computer. Once you have control you can change the password or manipulate the data.
Tips to secure your X account
- Secure password: Use a strong, unique password for your X account. Combine upper and lower case letters, numbers, and special characters to create a strong password. Avoid using personal information such as names or dates of birth.
- Two-Factor Authentication (2FA): Enable two-factor authentication on your X account. This feature requires an additional code, which is sent to your mobile phone or email, in addition to your password to log in. This adds an extra layer of security.
- Keep your devices safe: Make sure the device you access X from is protected with up-to-date antivirus software and a firewall. Keep your operating system and all applications updated to avoid security vulnerabilities.
- Be careful with links and attachments: Don't click on suspicious links or download files from untrustworthy sources, even if they come from known contacts. Hackers often use phishing techniques to trick you into gaining access to your account.
- Check your privacy settings: Regularly review and adjust your account privacy settings. Limit the visibility of your tweets and who can send you direct messages. Also, check for third-party apps with access to your account and revoke permissions for any you no longer need.