|
Hack Instagram
Explanation Images
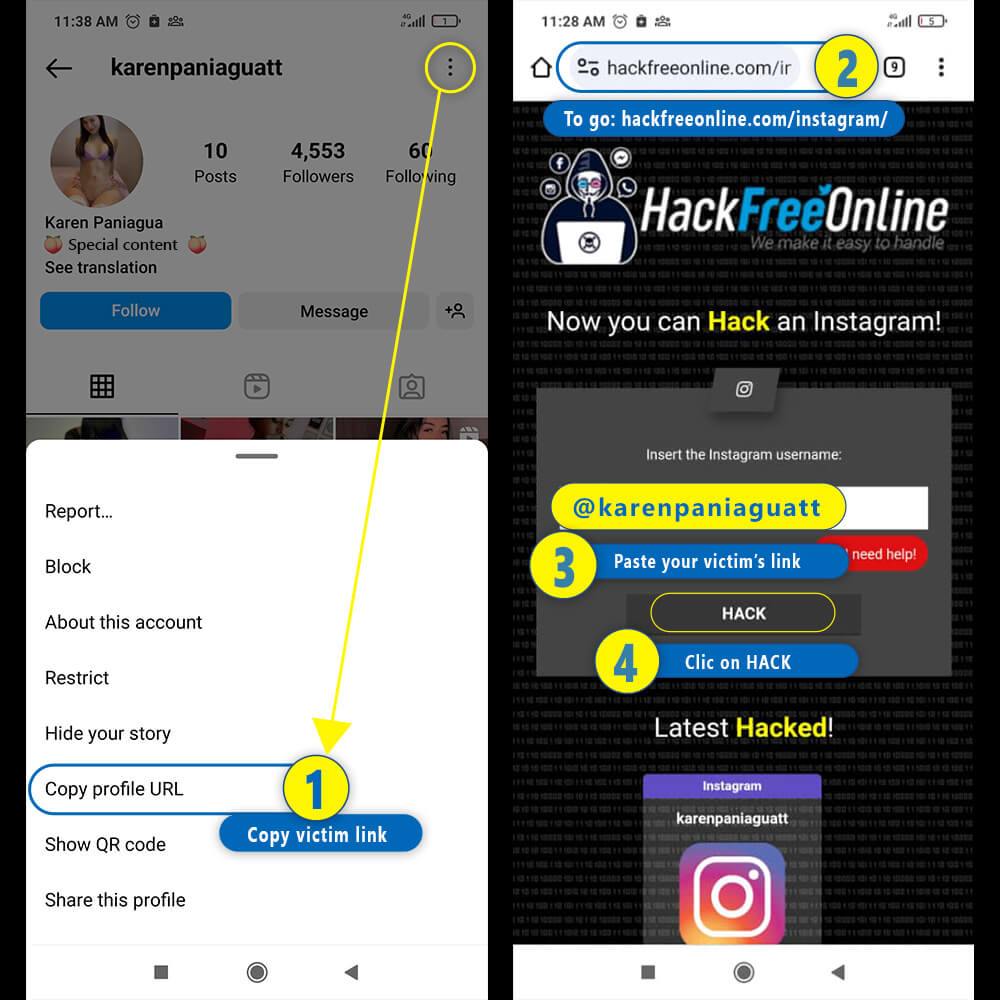
📱 Steps to Hack Instagram from a mobile phone
- 1️⃣Enter Instagram and copy the link of the profile you want to hack by clicking on the three dots
- 2️⃣Go to www.hackfreeonline.com/instagram
- 3️⃣Paste your victim's profile link in the main field
- 4️⃣Finally, click on "Hack"
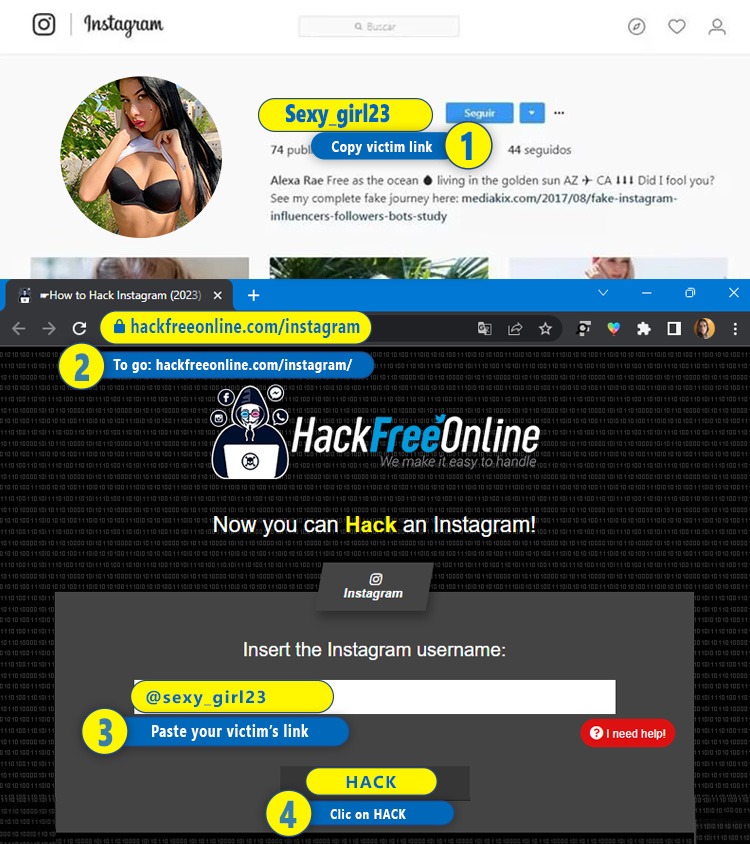
💻 Steps to Hack Instagram from a computerWith this system you can hack any Instagram account in a few minutes, without having to download any program or pay for anything. Likewise, you do not need to have computer experience or knowledge to use this website.
- 1️⃣Access Instagram and copy the link of the person you want to hack
- 2️⃣ Go to www.hackfreeonline.com/instagram
- 3️⃣Paste your victim's link in the main field
- 4️⃣Finally, click on "Hack"
Do you want to hack an Instagram account in 2026? Then you'll be interested in practicing these easy tricks we have for you.😜
Hack Instagram with Phishing
A second strategy to hack an Instagram account is Phishing, this technique that consists of tricking users into entering their access credentials on a false website that imitates the appearance of the social network.
This way, hackers can steal Instagram accounts and use them for malicious purposes, such as spying, extortion, spreading spam or malware, etc. Phishing to hack Instagram is usually carried out through emails that pretend to be sent by the platform itself.
These emails include a link that redirects the user to the fake web page, where they are asked to enter their login details.
Phishing to hack Instagram is a method widely used by cybercriminals, as it allows them to access accounts with many followers or influence and take advantage of the trust they generate among their contacts.
SCAM
One of the pages to hack Instagram through Phishing is Login-online.me. This website offers links to different fake login services, which are known as SCAM.
A SCAM is a type of program that has the ability to obtain other people's passwords and is used to hack social media accounts such as Instagram.
The operation of these programs is very simple, since they are based on a small part of Social Engineering, which consists of manipulating a user so that they themselves provide their information and personal data without realizing it.
The procedures for creating a SCAM are as follows:
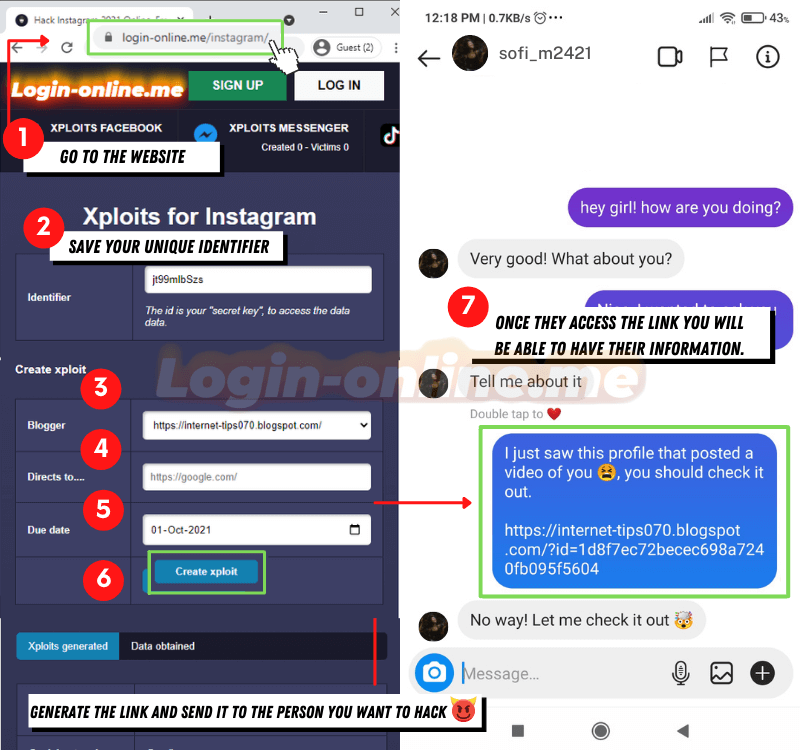
- Go to the website https://login-online.me/instagram/
- Save the identifier, this will be your access key to the results obtained.
- Choose the link of your preference in the Blogger section
- Select the page to which the user will be redirected when clicking the link.
- Select the expiration date
- Click on “create SCAM”
- Send the link accompanied by a message that generates trust
- Wait for the victim to log in the website
- Once the user has logged in, you can find the password in “Data obtained”.

Hack Instagram with saved browser passwords
If you have access to the victim's computer or mobile device, there are some options that you can use to your advantage to hack Instagram. It consists of obtaining the passwords saved in the browser, we will explain how to do it.
For this trick you must use the Chrome browser, since it offers the option to store passwords. In this password manager you can find various websites or apps, including the Instagram account.
To use this option, you must enter the following address in Chrome: chrome://password-manager/passwords or following this link: Password Manager
Hack Instagram with Keylogger
A keylogger is software that records the keystrokes made on a computer keyboard, often without the user realizing or authorizing it. A keylogger can be a good tool to steal personal data, passwords or information from an Instagram account.

We recommend you use ethicalkeylogger.blogspot.com to hack Instagram, you just have to install the software on the device of the person you want to spy on. Whether through a malicious web page, a contaminated application or direct access to the computer.
Then, you must wait for the person to log into their Instagram account and obtain the credentials they type. Finally, enter the Instagram account with the credentials obtained.
Hack Instagram with FORM-GRABBING
Hack Instagram with FORM-GRABBING It is a technique that consists of obtaining the data that is entered in a web form. Like the Instagram username and password, through a harmful code that is executed in the browser of the person you want to hack.
This code may be hidden on a deceptive web page, in an advertisement, or in a browser extension. The purpose is to send the data obtained to a remote server that the hacker controls.
This method can be undetectable to the victim and for certain antiviruses, and can affect any web platform, not just Instagram. Additionally, it can give you access to private Instagram account information such as photos, videos, chats, and GPS location.
Hack Instagram with malware and viruses
Viruses and malware have been very common methods to infiltrate devices and hack an Instagram account. In this section we discuss the most common types of attacks:
- Malware: refers to any harmful software that is intended to infiltrate or damage a computer or information system. By doing so you can have access to a Instagram profile.
- Virus: is a type of malware that spreads by infecting other files and altering the normal functioning of a device. To run, it requires user intervention, for example when opening an attachment or downloading a program.
- Spyware: It is a type of malware that monitors user activity and sends this information to third parties without the victim's consent.
- Adware: It is a type of malware that displays unwanted advertisements in the user's browser or desktop. To then direct the victim to harmful websites or install programs that can steal their Instagram credentials.
- Trojans: They are harmful programs that pretend to be normal files, but that carry out dangerous operations on your computer or mobile phone. They can have various functions, such as stealing data from Instagram or installing dangerous programs.
- DNS poisoning: is a technique that consists of changing Domain Name System (DNS) entries to direct the user to false or harmful websites. In this way, the hacker can trick the user into entering their Instagram credentials on a web page that simulates the original.
- Cookie theft: By stealing cookies, the hacker can enter the user's Instagram account without needing to know their password.
- SQL injection: consists of introducing harmful SQL code into a database query. If the database contains the victim's Instagram credentials, the hacker can access their account.
- Spoofing: It consists of impersonating the identity of another person or entity in an online communication. For example, the hacker can send an email posing as Instagram and ask the user to confirm their details or change their password.
- Hijacking: is taking control of an active web session between the user and a website. For example, the hacker can intercept data packets sent between the user and Instagram to modify or steal them.
- Spoofer: A spoofer can change the hacker's IP or MAC address to hide their real identity or location.
Tips to Keep a Instagram account safe
These are some of the most common methods to hack Instagram, but they are not the only ones. Hackers are always looking for new ways to attack the security and privacy of users, so we share you some tips to protect Instagram:
- Avoid weak passwords: Use strong passwords, avoiding personal information. Combine letters, numbers, and symbols, and change your password regularly.
- Two-Step Authentication: Add an extra layer of security with two-step authentication, which requires a one-time code via SMS or app when signing in on new devices.
- Session Control: Review login activity and close any unknown or unused sessions. Examine Instagram emails in the last 14 days for phishing attempts.
- Official App: Download Instagram only from Google Play or the App Store to avoid unofficial apps that could compromise your security.
- Avoid Fake Sites: Verify the authenticity of links or messages that request login. Fake sites may have errors, suspicious domains, or different designs. Stay cautious.