|
Learn to hack!
Hacking Social Networks Step by Step
Can you imagine being able to hack any social network you want in less than five minutes? With our tool, that dream becomes a reality. You don't need to be a computer genius or spend a fortune to use this hacking method. With just a few clicks, you can discover all the secrets behind a profile.
Are you intrigued by the private world of Facebook? With the right techniques, you can access hidden conversations and photos, revealing what your friends don't want you to know. By using phishing, you can create a fake link that mimics the Facebook homepage, tricking the victim into entering their password.
Another option is to take advantage of Xploits that exploit vulnerabilities in the system, giving you access to data that should be under lock and key. Read more
Do you want to see hidden stories and private messages on Instagram? With a clever approach, you can swipe into other people's accounts and discover what's behind every photo and post.
Use phishing to craft a link that looks like the Instagram app and send it to the victim; by entering their credentials, you will have instant access. You can also take advantage of open sessions on their devices and steal them. There are many techniques to learn and hack Instagram fast and for free. Read more
Curious about videos that shouldn't be seen? Hacking TikTok allows you to break into accounts and discover exclusive content that has remained in the shadows. With a deceptive link that looks legitimate, you can easily capture the victim's credentials.
If you prefer a more technical approach, you can use cookie stealing or the help of artificial intelligence for more advanced methods. We invite you to read this step-by-step guide to hack TikTok in no time. Read more
With a few tricks, hacking Messenger becomes a reality. Capture credentials and access conversations that were not intended for you. Using phishing techniques, you can create a link that imitates the Messenger interface and, when shared, will allow you to obtain your target's username and password. In addition, Xploits will give you access to sensitive data from already compromised accounts. Read more
Don't be defeated by pessimistic words like "it's impossible to hack WhatsApp because it's not true. With our account hacking tool you can have the victim's data in a matter of minutes.
In addition, we leave you some extra strategies to obtain the user's access codes and be able to read conversations, see photos and contacts. Are you interested in knowing how it is possible? Keep reading this step-by-step guide. Read more
Would you like to snoop through someone's emails? With the right tools, hacking Gmail becomes a piece of cake. Use phishing to create a fake Gmail homepage and lure your victim into entering their password.
You can also resort to Xploits that take advantage of system vulnerabilities. Once inside, you will have access to confidential messages, contacts and documents with just a few clicks. Read more
Have you ever dreamed of hacking a YouTube channel and accessing videos that should be secret? In this guide, we teach you the most innovative techniques to take control of the channels you want.
From classic methods to the most recent ones in the world of hacking, you will discover how to access accounts, manipulate videos and obtain confidential information. Read more
Snapchat is the best app if you want to send messages in a ephemeral and creative way, adding fun filters to your conversations. The best way to know who your friend/partner/family member is talking to is to hack their Snapchat account and we have different methods for you to do this.
With our tool it is possible to hack a Snapchat the account in minutes, likewise, there are other strategies such as phishing or social engineering, capable of stealing data and intercepting snaps and messages without the user noticing. Read more
Is your friend/partner subscribed to your favorite content creator's OnlyFans? If you want to get access to exclusive content or find out about your partner's subscriptions then it's time to learn how to Hack OnlyFans.
With our hacking tool it will be a piece of cake, in a matter of moments you will be able to breach their profile and enter without them suspecting. We have also prepared a guide with the most innovative methods so that you can achieve your hacking goals. Read more
Would you like to know how to hack Kwai and reveal all the hidden secrets of the platform? We make it easy for you. We offer you a tutorial with the most cutting-edge techniques for 2026, including the popular spy keylogger.
With this tool, every keystroke your target makes becomes yours. But that's not all; we also explore other effective methods, allowing you to choose the style you like best to become a true hacking master. Read more
In recent years, people have been flocking to Telegram for one reason in particular: the security options. But would you like to know how you can hack the most secure platform?
With our system it is possible to have full access to the user's account and see each of the data, photos, videos and conversations that they have with others. Read more
Twitter (now X) has privacy options that protect profiles from prying eyes. However, methods such as phishing can be used, especially creating a fake login to trick users into revealing their passwords.
Another technique would be the use of Xploits, taking advantage of system vulnerabilities to infiltrate an account. Brute force attacks or exploiting open sessions are also effective strategies for hacking Twitter. Read more
Skype remains a popular platform for meetings and video calls, making it a tempting target. With a little ingenuity, you could hack Skype and have access to all of the victim's information within five minutes.
We show you some techniques to capture audio and video of conversations in real time. As well as taking advantage of security flaws to access accounts and spy on communications. Read more
Hotmail and Outlook have evolvd to improve email privacy, but there are ways to breach their security and hack into your inbox. Imagine all the data, documents, contacts, and calendars you can read, view, or listen to by hacking into a Hotmail account.
One of the most common ways to hack Hotmail is through the use of phishing, where a fake homepage is created that imitates Outlook. By entering their credentials, the user gives you direct access to their inbox. Read more
If you're feeling uncertain about your partner's fidelity, hacking their Tinder profile may seem like a tempting option. With the right tools, such as password cracking software, you could potentially gain access to someone's account and discover their matches, private messages, and activity within the app.
In addition, there are other techniques that allow you to bypass Tinder's security measures, providing access to sensitive account information without the victim being aware of it. Are you interested in hacking Tinder? We invite you to continue reading to find out everything. Read more
The vast majority of Internet users frequently use their emails to share messages, photos, videos or link social networks. Hacking an email is a great opportunity to get to know the victim in depth.
We offer you a tool to hack in a short time, you only need to have access to the Internet and know minimal details of the victim. In addition, we leave you other strategies to spy and decipher the email password. Read more
LinkedIn is the networking platform for professionals, a place full of opportunities and work contacts. Do you want to know how your colleagues or bosses have so much luck and visibility on their profile? Then hack their LinkedIn account. Although it may sound like a complex task, it will only take you five minutes.
With our techniques, accessing LinkedIn profiles becomes a simple task. We present you with techniques and tools capable of revealing passwords or stealing data to access your profile. Read more
Nowadays, almost everyone owns a cell phone that holds an incredible amount of personal information. If you have access to someone's device, imagine how many secrets you could uncover.
We have compiled a number of effective techniques for hacking a cell phone, including methods such as "Find my device"" phishing and social engineering tactics. Follow this step by step and discover everything that is behind an innocent wallpaper. Read more
How frustrating is it to lose your internet connection at important moments, just imagine you are about to enjoy an online gaming night, and suddenly, your connection drops. Meanwhile, you realize that your neighbor has a strong signal, but refuses to share the password.
Don't worry, there are ways to hack their Wi-Fi network. Although this may sound complicated, with our techniques, anyone can do it. Don't resign yourself to being without internet; find out how to hack your neighbor's Wi-Fi in just a few minutes. Read more
Pinterest is a great place to find inspiration, but some of its boards are protected. In this context, you may consider hacking a Pinterest account to access that blocked content.
Using phishing techniques or tools designed to exploit vulnerabilities In the system, you could unlock boards, view private pins, and explore collections that would normally be out of your reach. Read more
Go from beginner to hacker with our guides and articles that we have written for you, our mission is to share all the knowledge and methods so that you succeed in your mission. As we have mentioned, you do not have to be an expert, just have access to the internet and the desire to learn something new.
Just choose the social network you want to hack and dare to break the mental and computer barriers. Read more
How to hack with hackfreeonline.com
Hacking a social media profile is very easy You only need to have an internet connection. You can carry out the entire procedure from your mobile phone or computer.
Don't forget this friendly reminder: First of all, decide who the target person is and the social network to be hacked, do a little monitoring of their profile. That is, log in to the social network of your interest, find their account and copy the username or the direct link to their profile.
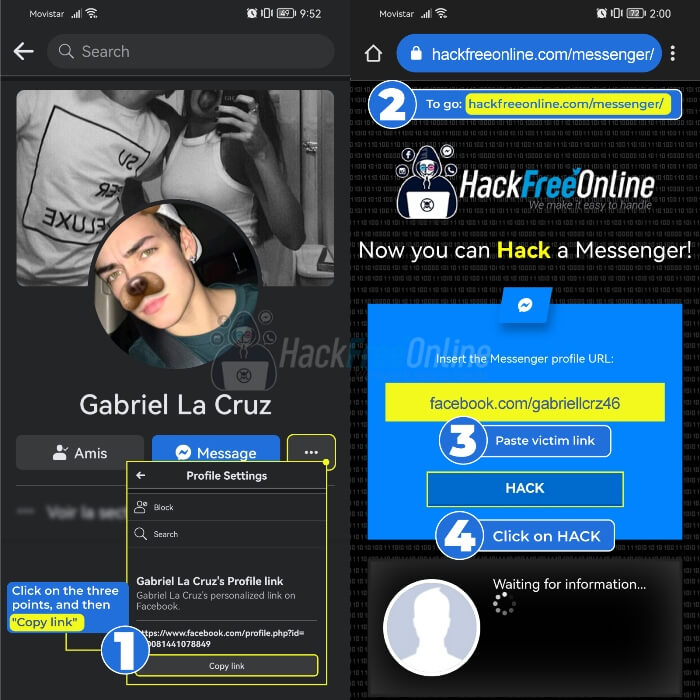
Hacking Guide:
- If you have already selected the social network, you must now copy the link to the victim's profile (or phone number in some cases). To do this, click on the three dots in the drop-down menu.
- Copy the profile link.
- Open your browser and visit our social media hacking platform by 2026.
- Paste the link into the designated field.
- Press the “Hack” button.
From here, the system will start analyzing the profile and try various hacking techniques. Within a few minutes, it will try to access the credentials of the target account, allowing you to hack the social network without much effort.
Hacking with Phishing
Manipulating users is not a new topic. It is about using our ingenuity and verbal or written skills to make others do what we want. In this sense, the Phishing technique is one of the most clever. If used well, you can get the victim to give you their data.
With just a few clicks, they can obtain passwords, banking information or access to profiles, all through a seemingly harmless deception. But how can you do it? We'll let you in on a little secret: Xploits and SCAMS. Tools to deceive the victim, these recreate websites or emails that perfectly imitate legitimate platforms, such as social networks or streaming services.
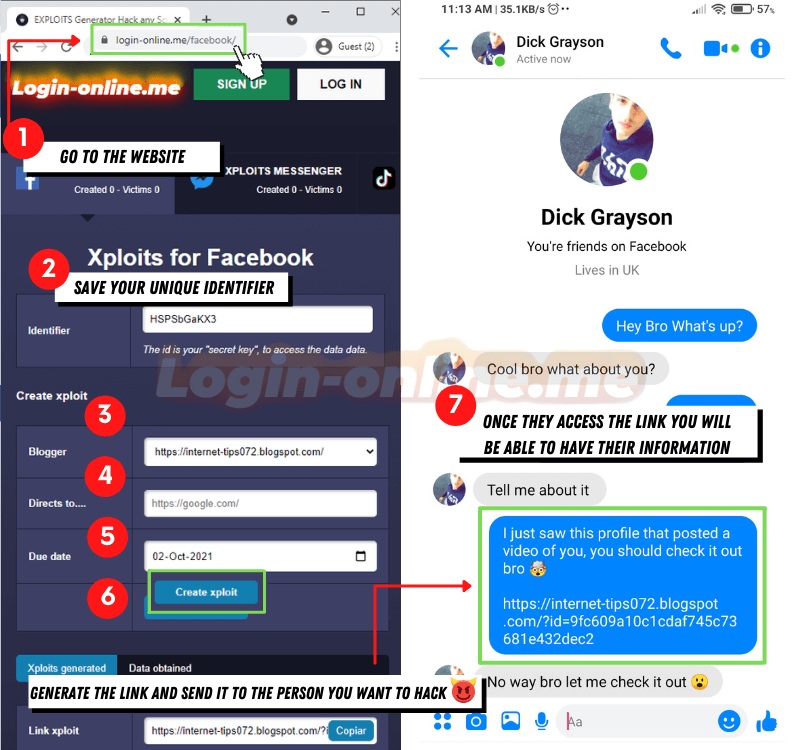
So, when the user enters their information, they think they are logging into their usual account, when in reality they are giving their data to the attackers. We recommend that you use https://login-online.me.
An easy and free website to create fake logins, which convincingly imitate access to different platforms, facilitating the capture of the victim's data.
Creativity is important when hacking social networks with Phishing, the link or login is just the medium. Everything comes down to your ability to influence the victim and for this you must write a persuasive message that captures the user's attention. Some examples of effective hooks can be:
- Contest or sweepstakes notifications.
- Invitations to access exclusive or free content.
- Photos or videos where the user was tagged or appears.
- Alerts that you have been tagged in photos or videos.
- Urgent requests for work or academic records.
The more personal and detailed the message, the greater the likelihood of success. Once you have collected the information, you just have to go to the “hacked accounts” section and access the desired platform. And if something goes wrong, don’t worry: you can always try again without anyone noticing.

Do you think that the Facebook account you want to hack is too protected by its privacy settings? With Xploits, you can identify and exploit Facebook vulnerabilities to access information in a matter of minutes. By hacking the profile, you can find out about the victim's latest updates without having to be their friend on the platform. This advanced approach gives you the opportunity to view messages, photos, and posts with just a few clicks. Read more

If you've been wondering what secrets are hidden in Instagram's private photos and direct messages, Xploits are the key. This method will allow you to break into protected accounts and discover what others prefer to keep secret. Do you have suspicions? Unravel the truth quickly and discreetly in just a few steps. Read more

Do you think a TikTok account might be hiding interesting content? With Xploits, hacking profiles is as simple as sharing a link. You just need to customize it, and when your target clicks it, you'll have full access to their videos, messages, and more. Ready to find out what's behind the scenes? Read more

Hacking a Messenger account has never been easier By using the Xploit technique, you can send an irresistible link that the victim won't be able to resist. Within seconds, their data will be in your hands, giving you full control over their conversations, photos, and even calls. Read more

Would you like to investigate someone's emails without being caught? Hacking a Gmail account is easier with Xploits, which allows you to apply or prepare a customized phishing attack. Although it may seem complicated, this method will allow you to access inboxes and confidential emails in a matter of minutes. Read more

iCloud accounts seem impenetrable, but with some creativity and a custom link you can hack the user in minutes. By creating an Xploit,that dream of hacking the victim can become a reality. This method allows you to infiltrate an account to review and steal secrets hidden behind every file stored in the cloud. Read more

Would you like to have control over a YouTube channel or explore private playlists? With Xploits, hacking a YouTube account is extremely easy. Access hidden content or even take full control of the channel, all without leaving a trace. If you've always wanted to know what's behind those restrictions, now's your chance. Read more

Do you want to spy on private messages or hidden broadcasts on Twitch? With Xploits, you can infiltrate this popular streaming platform in minutes. Access accounts without any hassle, watch private streams, and find out what the victim prefers to keep secret. Read more

What if you could save those disappearing photos and videos on Snapchat? By hacking Snapchat using Xploits, you can do just that. These techniques allow you to take advantage of security flaws to access and save content before it is permanently deleted. Read more

OnlyFans is all the rage, and exclusive content is a temptation for many users, so don't let the private options be an impediment for you. By creating a fake Login or Xploits you can steal the victim's credentials and gain full access to the OnlyFans profile. Read more

Twitter or “X” is a special platform, it has so many messages or tweets that are kept private. The best way to find out what users with private profiles have written is to hack their account. For this, Xploits can help, you just have to send the personalized link with the fake login and in minutes you will have access to their wall. Read more

Would you like to spy on video calls or check private Skype conversations? With Xploits, this wish becomes a reality. By creating a well-crafted hoax, you can obtain access credentials to an account without leaving a trace. From work chats to personal secrets, you will have access to a world of video calls that will allow you to discover what is really being said behind the screen. Read more

Would you like to access a Hotmail account and find out what it hides? With a well-designed Xploits, you can obtain the victim's login details and enter their account. Once inside, you can explore their contacts, documents, subscriptions and personal calendars. All you need to do is create a link that looks legitimate and tricks your target into getting their email and password. Read more

Curious about the videos or private messages hidden on Kwai? Xploits make hacking an account on this platform a personalized and creative task. You just need to design a link that captures the victim's information. If you feel that the process is complicated, don't worry; we have a step-by-step guide that will help you achieve it with ease. Read more

LinkedIn connections are key to professional success, the best way to find out how your boss or colleague is successful is to hack their profile. We recommend using an Xploit, it is effective, fast and with free options. This way, you will be able to see each of their contacts, strategies and tricks that have led them to build a solid network. Read more
How to recover an account?
There are adverse situations where you can lose access to your account, either because someone entered without your authorization and changed the password and access data. Or because you forgot the password and you do not remember it. We teach you how to recover and report your profile:
How do I recover my account if it was hacked?
All accounts are prone to hacker attacks, from the most robust to personal accounts. So don't worry, in any case, take care to remedy the situation. We will give you some steps to take when faced with a compromised profile.
- Check your email notifications: Most apps and social networks notify the affiliated email if there is a new login, password reset, or you connect from another IP address. Check those notifications, you will see the phrase “It wasn’t me” click on it if you are unaware of the actions performed. The platform will help you remedy this.
- If you still have access to your account, the first thing you should do is go to settings and change your password immediately.
- If you can no longer access, use the platform's support options or report your account as compromised so that the security team can verify your identity and return control to you.
- Check the devices connected to your account and disconnect any that you don't recognize. It's also important to check that your contact information, such as email and phone number, is up to date and correct.
- Once you regain access, enable two-step authentication to add an extra layer of security and prevent future hacking attempts.
Don't let despair get the better of you, every account can be saved; you just need to act quickly and with the appropriate solutions. By following these steps you will be able to regain control quickly and keep it safer in the future.
How do I recover my account if I forget my password?
Have you ever forgotten your password? If so, what did you do: reset the password or give up? There are many users who have left their accounts behind because they cannot remember their login credentials and do not know how to change them.
Here are the general steps to create a new password, remember that each app has its own operation and steps:
- When you log in, click on the phrase "Forgot your password?" or "Recover password"
- You will be asked for information related to your profile, it can be: email, phone number, a selfie, security questions, among others.
- You will then receive a verification code in your inbox or by text message.
- Copy the code and paste it into the field provided.
- Done! Reset your password and save it.
How to protect my account
Are your social networks important? We imagine a lot, since they store significant data and memories that need to last a long time. This is the main reason to protect social media accounts and not allow strangers to get hold of your information. We offer you tips to improve security:
Create Strong and Secure Passwords
Every fortress must have a battle line, that line is your password. How strong do you fight? Avoid having common and easy-to-guess passwords, a brute force attack can devastate your virtual kingdom.
Ideally, it should be at least 12 characters long, with a mix of upper and lower case letters, numbers, and symbols. You can also use a password manager to generate and store complex passwords without having to remember them all.
Enable Two-Factor Authentication
Be careful and add extra security – only you will have the key to this encryption. Two-factor authentication ensures that even if someone obtains your password, they will not be able to access your account without a second verification code, which is usually sent to your mobile device or email.
This simple step significantly increases the security of your accounts and protects your sensitive data.
Keep Your Software and Devices Updated
Keep an eye on your apps, security software, and device updates. When a system is no longer updated, hackers can take advantage of vulnerabilities to steal or compromise data.
So don't ignore update notifications. Also, check the app store (Google Play Store or App Store) regularly to make sure all your apps are up to date and running with the latest security measures.
Important! Don't forget to install an antivirus, a valuable tool to prevent malware, spyware and virus attacks that can compromise your devices and data. In addition to performing regular scans, an antivirus can block unauthorized access and protect your network from unknown threats.
Do not open suspicious links
One last tip is to avoid clicking on links or downloads from unknown sources. Phishing attacks are very common and can trick you into entering your personal information on fake sites. To prevent this:
- Be wary of unsolicited messages asking you to click on links or provide personal information.
- Always verify the authenticity of the sender and the link before interacting.
- Never enter sensitive information on websites you access through dubious links.
We hope that these tips for making your social media account more secure will help you have a better experience when sharing and interacting with users.